Introduction
Security Assertion Markup Language (SAML) is an XML-based authentication that provides single sign-on (SSO) capability between different organizations by allowing user authentication without sharing the local identity database. Parallels RAS 17.1 and newer support the SAML authentication mechanism.
SAML (2.0) SSO was introduced in Parallels RAS 17.1 supporting HTML5 initiated authentication using Web Client or Parallels Client for Windows. Parallels RAS 18 extends the client support for initiating SAML authentication using the default OS browser or the browser embedded in Parallels Client.
As part of the SAML SSO process, the new RAS Enrollment Server communicates with Microsoft Certificate Authority (CA) to request, enroll, and manage digital certificates on behalf of the user to complete authentication without requiring the users to put in their Active Directory credentials. Service providers and enterprises with multiple subsidiaries don’t have to maintain their own internal Identity Management solutions or complex domains/forest trusts. Integrating with third-party Identity Providers allows customers and partners to provide end users with a true SSO experience.
Supported delivery options are:
- Web Client
- Web Client initiated SAML for Windows
- Web Client initiated SAML for Mac and Linux
- Web Client initiated SAML for Android, iOS and iPadOS
- Parallels Client for Windows initiated SAML authentication
- Parallels Client for Mac initiated SAML authentication
- Parallels Client for Linux initiated SAML authentication
- Parallels Client for iOS/iPadOS initiated SAML authentication
- Parallels Client for Android initiated SAML authentication
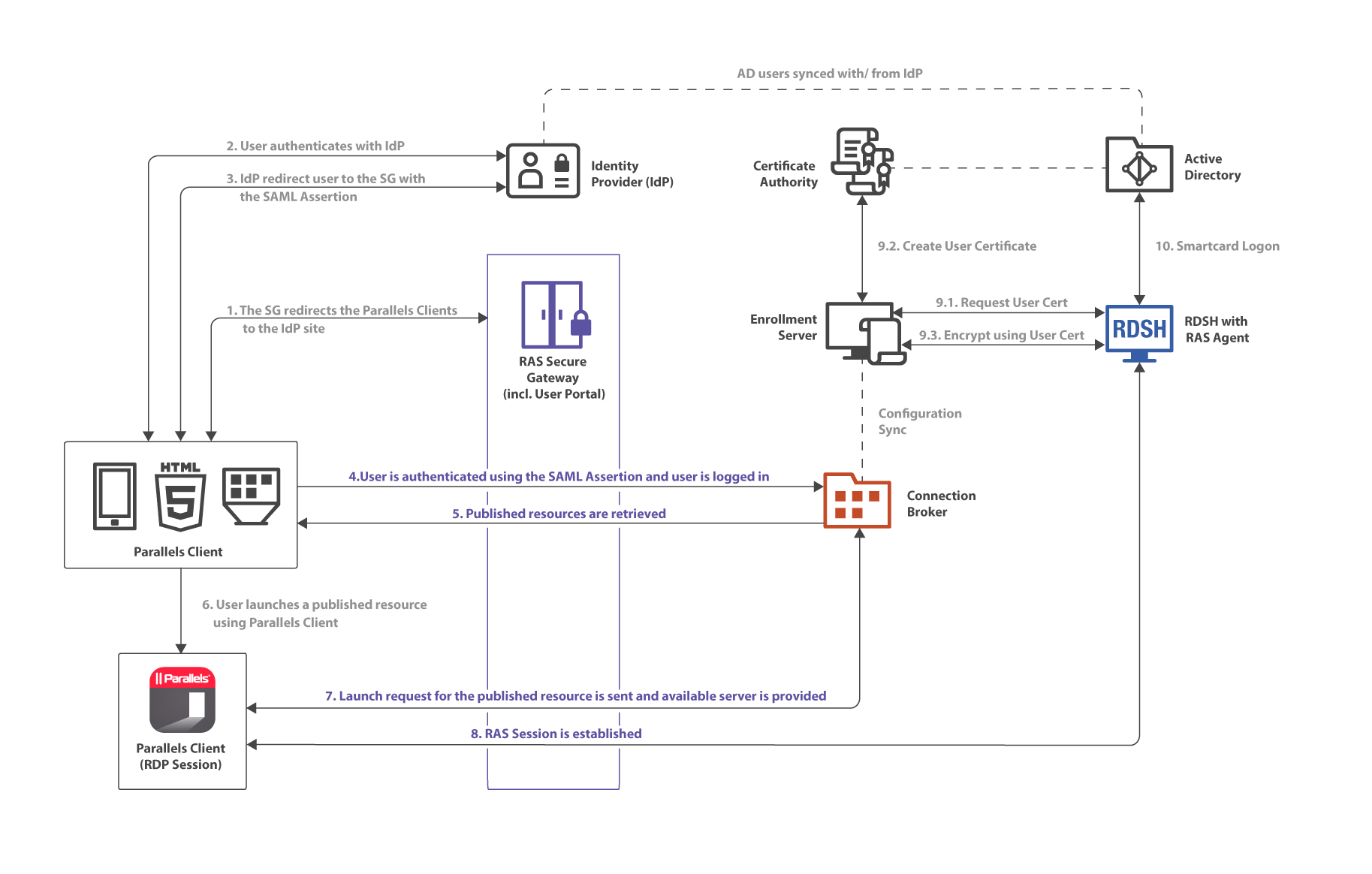
The below high-level logical diagram depicts SAML authentication and login process within a Parallels RAS environment:
The SAML authentication and login steps on the diagram above are:
- RAS Secure Gateway redirects the Parallels Client login request to the IdP site.
- The user authenticates with IdP.
- IdP redirects the user to the RAS Secure Gateway with the SAML Assertion.
- The user is authenticated using the SAML Assertion and the user is logged in.
- The list of the available RAS published resources is retrieved.
- The user chooses a published resource and launches it from Parallels Client.
- The launch request from the user is sent to the server side and the resource is started on the available server.
- A Parallels RAS session is established.
-
User certificate is processed:
- Certificate is requested.
- Certificate is created.
- Encryption is preformed using the certificate.
- Smartcard logon.