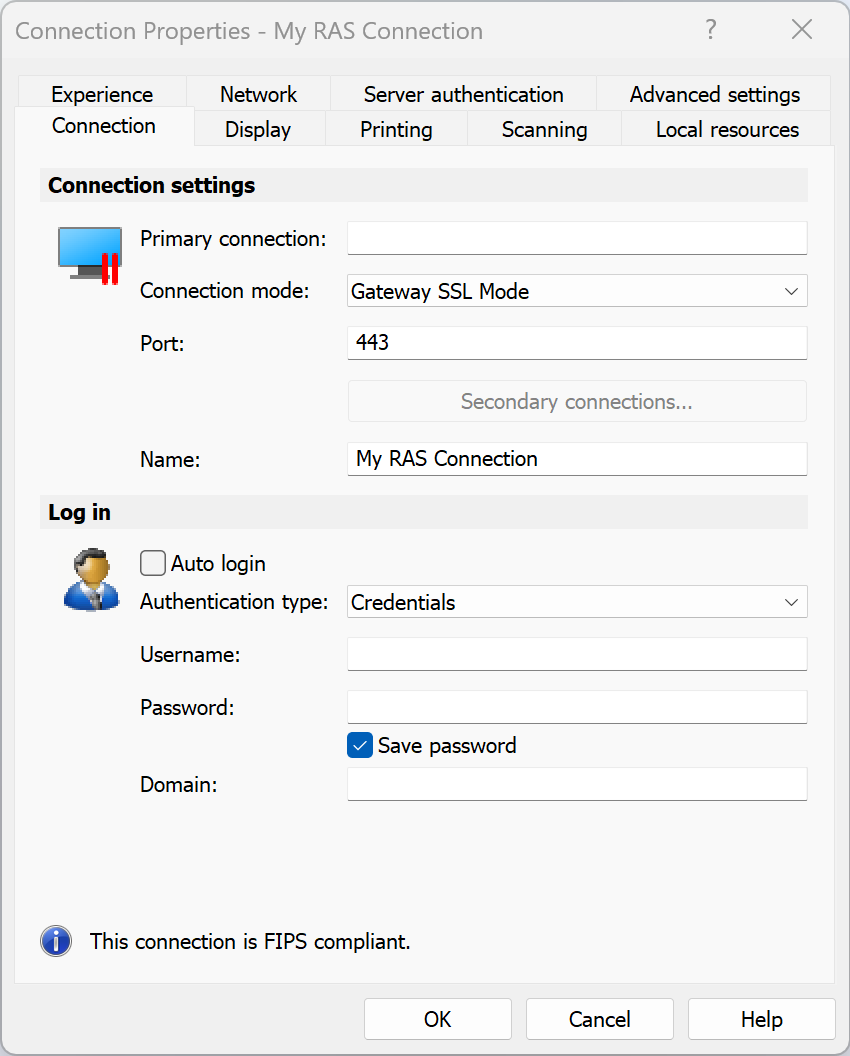
Connection
The Connection tab page allows you to specify connection properties and login information.
Configuring the Primary Connection
On the Connection tab page, configure the primary connection and one or more secondary connections.
The primary connection is what Parallels Client will use first to connect to the specified server. This should be the server where the primary RAS Secure Gateway is running.
To specify the primary connection information:
-
In the
Primary connection
field, specify the server name or IP address. To connect to a specific RAS Theme, specify its name after the server name or IP address separated by a slash. For example, workspaceus.parallelsras.net/theme1. If not sure which Theme you should use, ask your system administrator.
You can click the [...] button and select a server from the list. If the server is not listed, it means that the system administrator disabled this functionality on the server side. In such a case, specify the server by typing its name or IP address in the Primary Connection field.
-
In the
Connection mode
drop-down list, select one of the following options:
- Gateway Mode: Parallels Client connects to the RAS Secure Gateway and the session connection is tunneled through the first available connection. This mode is ideal for servers which are only reachable via the gateway and do not require a high level of security.
- Gateway SSL Mode: Same as the gateway mode above, but uses encryption to secure the data.
- Direct Mode: Parallels Client first connects to the RAS Secure Gateway for the best available terminal server and then connects directly to that particular server. This is best used when the Parallels Client and the terminal server are on the same network.
- Direct SSL Mode: Same as the direct mode above, but uses encryption to secure the data.
- In the Port field, specify the port on which the gateway listens for incoming connections. If the default value has been modified on the server side, you have to replace the default value here as well. Otherwise, leave the default value intact.
- In the Friendly Name field, choose and type a name of your choice.
Configuring a Secondary Connection
If the server you are connecting to has more than one RAS Secure Gateway, you can define a secondary connection, which will be used as a backup connection in case the primary connection fails.
To add a secondary connection:
- Click the Secondary Connections button.
- In the Secondary Connections dialog, click the Add button and specify a server name or IP address. This should be a server hosting a secondary RAS Secure Gateway (the primary gateway is used by the primary connection). You can click the [...] button and select a server from the list. If none are available (or if the desired server is not in the list), type the server info in the field provided.
- Select the connection mode and modify the port number if necessary. Click OK .
- Back in the Secondary Connections dialog, you can move connections up or down the list if you have more than one. If the primary connection cannot be established, Parallels Client will use secondary connections in the order listed.
- Click OK .
Configuring the Logon Information
In the Logon section, specify the following properties:
- Select the Auto start option to enable Parallels Client to connect automatically (using this connection) on startup.
-
In the
Authentication type
drop-down list, select the desired method of authentication:
- Credentials : Select this option and then enter the username, password, and domain information. You will be authenticated on the remote server using the specified credentials.
- Smart Card : Select this option to authenticate using a smart card. When connecting to the remote server, insert a smart card into the card reader and then enter a PIN when prompted.
- Single Sign-On : This option will be included in the list only if the Single Sign-On module is installed during Parallels Client installation. Select this option to use local system credentials to connect to the remote server.
- Web : Select this option to use the SAML SSO authentication.