Learning Private Networks
By default, all virtual machines and Containers on the physical server operating in the host-routed mode can access each other even if you connect them to different subnets. For example, if Container 101 has the IP address of 100.10.10.101 and the
MyVM
virtual machine has the IP address of 100.10.11.102 and you set the subnet mask for them to 255.255.255.0, the virtual machine and Container will be able to communicate with each other, though they technically belong to different subnets: 100.10.10.0 and 100.10.11.0.
Note: You can also include virtual machines and Containers operating in the bridged mode in private networks. For information on how you can do this, see Setting Up Private Networks .
In Parallels Cloud Server 6.0, you can create the so-called private networks . Within these private networks, you can make subnets and connect virtual machines and Containers to these subnets so that the virtual machines and Containers from one subnet will not be able to access virtual machines and Containers from other subnets, virtual machines and Containers outside the private network, and computers on external networks. The following figure demonstrates a system containing a private network:
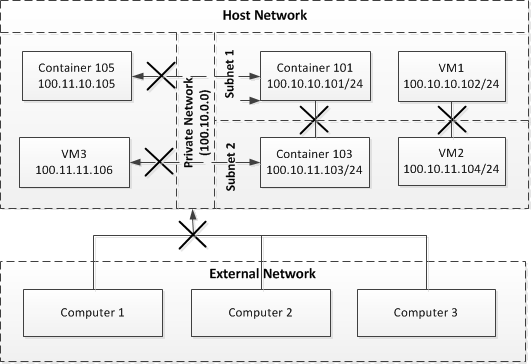
In this example, the network is configured as follows:
- A private network ( Private Network ) is created within the physical server network ( Host Network ).
- The private network contains two private subnets: Subnet 1 and Subnet 2 .
- Container 101 and VM1 are connected to Subnet 1, and Container 103 and VM2 are joined to Subnet 2.
- Container 105 and VM3 do not belong to the private network.
- The physical server network is connected to an external network ( External Network ) that contains computers Computer 1 , Computer 2 , and Computer 3 .
In this network, Container 101 and VM1 can access each other, but cannot connect to Container 103, Container 105, VM2, and VM3. Container 103 and VM2, in turn, can also access each other, but cannot connect to Container 101, Container 105, VM1, and VM3. None of the virtual machines and Containers in the private network can access computers on the external network.
Network Across Multiple Nodes
The example above deals with a private network created within one physical server. However, private networks can span virtual machines and Containers on two or more servers. The following figure demonstrates such a network:
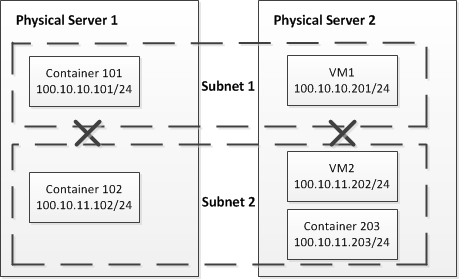
In this figure, the private network also includes two private subnets—Subnet 1 and Subnet 2, but the virtual machines and Containers included in these subnets reside on two physical servers. Container 101 and VM1 are joined to Subnet 1, and Container 102, Container 203, and VM2 are joined to Subnet 2. The virtual machine and Container on Subnet 1 can connect to each other but cannot access the virtual machines and Containers on Subnet 2, and vice versa.
Weak Private Networks
By default, when you create a private network, no virtual machine or Container on this network can access
- virtual machines and Containers that are joined to other subnets in the private network,
- virtual machines and Containers that are not part of the private network,
- computers that are located on external networks.
However, you can configure a private network so that its virtual machines and Containers cannot communicate with virtual machines and Containers on other subnets in the private network but can connect to virtual machines and Containers outside the private network and to computers on external networks. Such private networks are called weak private networks . "Weak" in this context means that these networks can be accessed by computers on external networks and are, therefore, more prone to security vulnerabilities and threats. The following picture demonstrates a system with a weak private network:
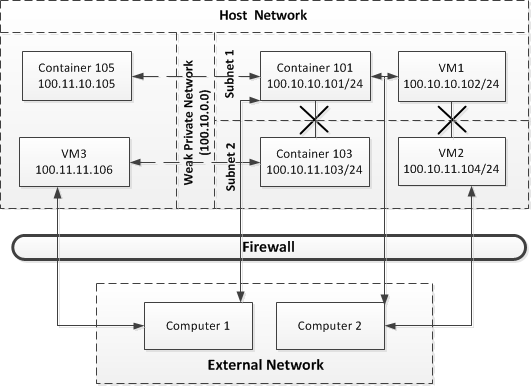
In this example, the private network on the physical server is divided into two subnets: Subnet 1 and Subnet 2 . Container 101 and VM1 are connected to Subnet 1, and Container 103 and VM2 are joined to Subnet 2. Container 105 and VM3 do not belong to the private network. Container 101 and VM1 can access each other, but cannot connect to Container 103 and VM2. Container 103 and VM2, in turn, can also access each other, but cannot connect to Container 101 and VM1.
All virtual machines and Containers in the private network can communicate with Container 105 and VM3 and, as they have public IP addresses assigned, can also access computers on other networks (for example, the computers Computer 1 and Computer 2 on the external network External Network ). To protect the virtual machines and Containers from possible security vulnerabilities and threats, the firewall is configured on the physical server, blocking unauthorized access to the virtual machines and Containers.
Global Private Networks
A global private network can serve as a foundation for other private networks that you will create inside it. All Containers and virtual machines in a global private network are isolated from each other, Containers and virtual machines in other private networks, and external hosts. However, Containers and virtual machines added to private networks inside the global network are allowed access as per those networks' limitations.
|
|
 Feedback
Feedback
|