Active Directory User Account Configuration
The enrollment agent user and NLA user must be created in Microsoft Active Directory. The following describes how to create these users.
Enrollment agent user account configuration
The enrollment agent user account is required in order to be used to enroll certificates through RAS Enrollment Server on behalf of the authenticated user.
To create the enrollment agent user and delegate permissions on AD container or OU, do the following:
- Open Active Directory Users and Computers.
- Create an enrollment agent user in AD.
- Right click on the container or OU where the user accounts logging in to the RAS environment reside and select Delegate Control .
- On the Welcome page of the wizard, click Next . On Users and Groups , click Add and enter the name of the enrollment agent account, then click OK and click Next .
-
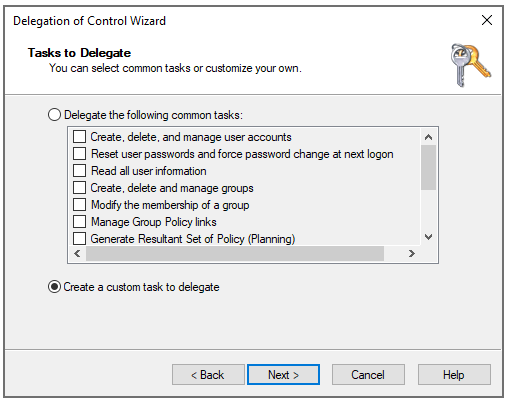
On the
Tasks to Delegate
page, click
Create a custom task to delegate
and then click
Next
.
-
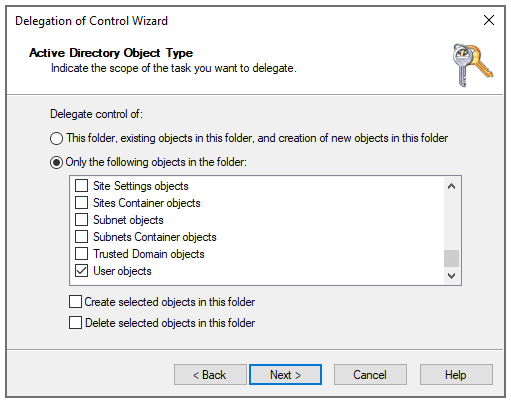
On the
Active Directory Object Type
page, click
Only the following objects in the folder
, select the
User objects
option, and then click
Next
.
-
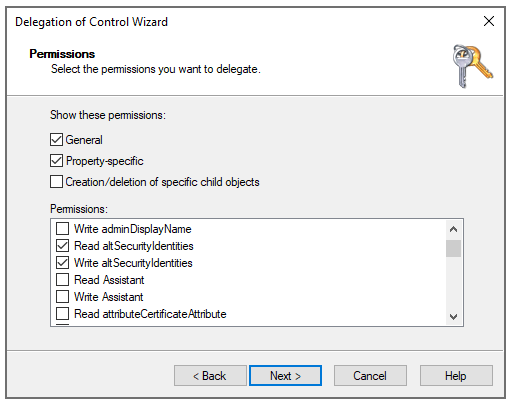
On the
Permissions
page, select the
Property-specific
option, then select the
Read altSecurityIdentities
and
Write altSecurityIdentities
options and click
Next
.
Note: The Alt-Security-Identities attribute either at domain (CN=USERS) or OU level where user accounts logging in to the RAS environment using SAML authentication reside. The Alt-Security-Identities attribute contains mappings for X.509 certificates or external Kerberos user accounts to this user for the purpose of authentication.
- On the Completing the Delegation page, click Finish .
NLA user account
The NLA User is needed to initiate the NLA connection with RD Session Hosts and/or VDI guests.
The NLA User must be a member of the Remote Desktop Users group and be granted the Allow log on through Remote Desktop Services permission. At the same time the NLA User must be prohibited to logon via Remote Desktop Services.
To exclude the NLA User account, it must be assigned the Deny log on through Remote Desktop Services user right.
To achieve both goals, you can use local or domain GPOs (linked to OU or domain wide).
A restart of the device is not required for this policy setting to be effective. Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on.
Group Policy settings are applied through GPOs in the following order, which will overwrite settings on the local computer at the next Group Policy update:
- Local policy settings
- Site policy settings
- Domain policy settings
- OU policy settings
Create a new GPO or use Default Domain Policy GPO as follows:
- Open the Group Policy Management Console (GPMC).
- Open or create a GPO linked with the OU where the RDSH or VDI objects reside.
- Navigate to Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment and open “Allow log on through Remote Desktop Services” option.
-
Choose to add User or Group..., add the NLA user and click OK.
Note: The option will override default settings (on workstation and servers: Administrators, Remote Desktop User; on domain controllers: Administrators) therefore do not forget to add the groups like local administrators group or domain admins group.
- Navigate to Computer Configuration > Windows Settings > Security Settings > Local Policies > User Rights Assignment and open the Deny log on through Remote Desktop Services option.
- Choose to add User or Group..., add the NLA user and click OK .
|
|
 Feedback
Feedback
|