Configuring Azure MFA
Depending on the user location there are four scenarios for the cloud MFA service:
|
User Location |
MFA in the cloud |
M FA Server |
|
Azure Active Directory |
Yes |
|
|
Azure AD and on-premises AD using federation with AD FS (is required for SSO) |
Yes |
Yes |
|
Azure AD and on-premises AD using DirSync, Azure AD Sync, Azure AD Connect - no password sync |
Yes |
Yes |
|
Azure AD and on-premises AD using DirSync, Azure AD Sync, Azure AD Connect - with password sync |
Yes |
|
|
On-premises Active Directory |
|
Yes |
An Azure account with Global Administrator role is required to download and activate MFA Server. Syncing with Azure AD (via AD Connect) or a custom DNS domain aren't required to setup an MFA Server which runs exclusively on-premises.
Users need to be imported into MFA Server and be configured for MFA authentication.
Parallels RAS authenticates users with MFA Server using the RADIUS second level authentication provider. MFA Server thus needs to be configured to allow RADIUS client connections from the RAS server.
The authentication process goes through the following stages:
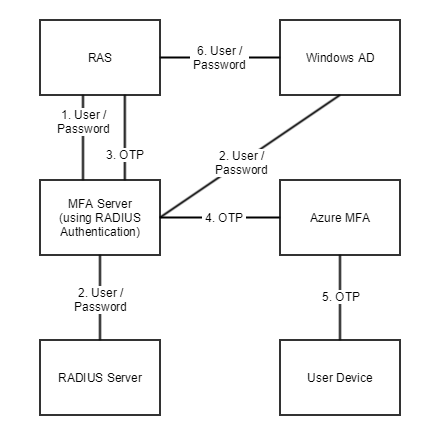
In stage 2 the user can be authenticated using either RADIUS or Windows AD. A prompt to enter the credentials twice (in stage 1 and 6) is avoided by enabling the option to forward the password.
|
|
 Feedback
Feedback
|