Configuring Parallels RAS to Use the DualShield Authentication Platform
To begin:
- In the RAS Console, navigate to the Connection / Second Level Authentication tab page.
- In the Provider drop-down list, select Deepnet .
- Click the Settings button.
- Click the Check Connection button to test that the authentication server can be reached and to verify that the RAS Console is registered as a DualShield agent. If you see the "DeepNet server not valid" message, you have either specified an incorrect server information or you need to allow auto registration of the Parallels components as a DualShield agent.
-
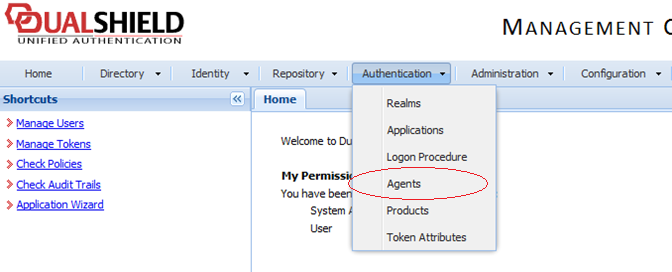
Go back to the DualShield Management Console and select
Agents
from the
Authentication
menu as shown below.
-
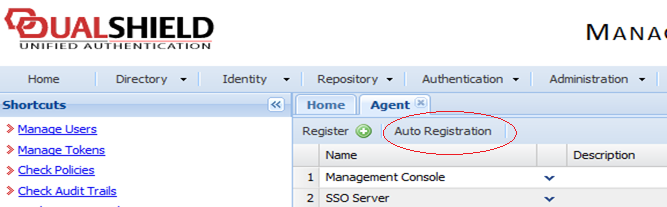
Select
Auto Registration
.
-
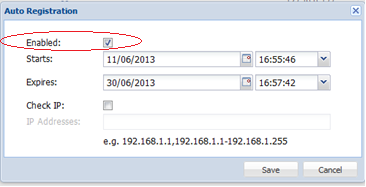
Select the
Enabled
option and set the date range.
-
Once the Agent Auto Registration is set, go back to the RAS Console and select
Yes
. You should see a message that the Dual Shield agent has been successfully registered.
Please note that All RAS Publishing Agents must be registered with Deepnet DualShield server. If you are using Backup Publishing Agents, you need to close all open windows until you can press Apply in the RAS Console. This will inform all the agents to self-register as DualShield agents.
- In the Deepnet Properties dialog, click the Applications tab and browse for the Application name previously created from the DualShield Management Console.
-
Click the
Authentication
tab and select how you want your users to be authenticated:
- Mandatory for all users means that every user using the system must log in using two-factor authentication.
- Create token for Domain Authenticated Users will allow Parallels Remote Application Server to automatically create software tokens for Domain Authenticated Users. Choose a token type from the drop down list. Note that this option only works with software tokens, such as QuickID and MobileID
- Use only for users with a DualShield account will allow users that do not have a DualShield account to use the system without have to login using two-factor authentication.
- Go back to the Connection > Second Level Authentication tab page.
-
In the Exclusion section, specify the exclusion rules:
- User / Group exclude list allows you to add users or groups within your active directory that will be excluded from using DualShield Authentication.
- Client IP exclude list allows you to add IP addresses or a range of IP addresses that will be excluded from using DualShield Authentication.
- Client MAC exclude list allows you to add MAC addresses that will be excluded from using DualShield Authentication. You can also specify a MAC address range using double question marks as a wildcard in any part of the address. For example, 00-14-22-01-23-??, 00-14-22-01-??-??, or 00-14-22-??-??-??.
- Connection to the following Gateway IPs allows you to set a Gateway where users connected to the Gateway will be excluded from using DualShield Authentication.
|
|
 Feedback
Feedback
|