Enabling SSL Encryption on a RAS Secure Client Gateway
The traffic between the users and the RAS Secure Client Gateway is always encrypted. The SSL/TLS tab page allows you to configure data encryption options. By default, a self-signed certificate is installed during the RAS Secure Client Gateway installation and TLS v1.0, v1.1, or v1.2 is used.
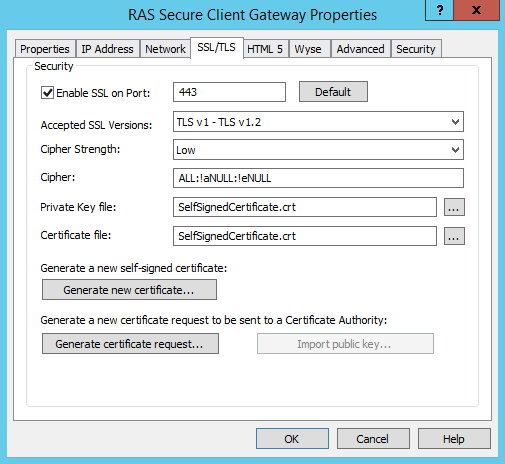
To issue a new self-signed certificate:
- Select the Enable SSL on Port option and specify a port number (default is 443).
-
(Optional) Select the SSL version accepted by the RAS Secure Client Gateway from the
Accepted SSL Versions
drop-down list (default is TLS v1 - TLS v1.2).
The available options are:
- TLSv1.2 Only (Strong)
- TLSv1.1-TLSv1.2
- TLSv1-TLSv1.2
- SSLv3-TLSv1.2
- SSLv2-TLSv1.2 (Weak)
- (Optional) Select the Cipher Strength as the certificate encryption algorithm strength of your choice.
-
Click the
Generate new certificate
button and enter the required details.
Note: To enable SSL using a certificate from a trusted authority, follow the procedure below.
- Click Save to save all the details and generate a new self-signed certificate. The private key file and Certificate file will be automatically populated.
- Click OK to save the options.
Using a Custom Cipher
Use the Custom Cipher field to specify a custom cipher string of your choice in accordance with the openSSL standards. Cipher strings used by Parallels Remote Application Server are described below:
Low: ALL:!aNULL:!eNULL
Med: ALL:!aNULL:!ADH:!eNULL:!LOW:!EXP:RC4+RSA:+HIGH:+MEDIUM
High:
- Min SSLv2 - ALL:!aNULL:!ADH:!eNULL:!LOW:!MEDIUM:!EXP:+HIGH
- Min SSLv3 - ALL:!SSLv2:!aNULL:!ADH:!eNULL:!LOW:!MEDIUM:!EXP:+HIGH
- Min TLSv1 - ALL:!SSLv2:!SSLv3:!aNULL:!ADH:!eNULL:!LOW:!MEDIUM:!EXP:+HIGH
- Min TLSv1_1 - ALL:!SSLv2:!SSLv3:!TLSv1:!aNULL:!ADH:!eNULL:!LOW:!MEDIUM:!EXP:+HIGH
- Min TLSv1_2 - ALL:!SSLv2:!SSLv3:!TLSv1:!TLSv1.1:!aNULL:!ADH:!eNULL:!LOW:!MEDIUM:!EXP:+HIGH
Note: By default only the connection between the gateway and the servers is encrypted. Change the connection mode to the Gateway SSL Mode from the connection properties on all Parallels Clients to also encrypt the connection between the users and the gateway.
Using a Certificate from a Trusted Authority for SSL
To enable SSL on a RAS Secure Client Gateway using a certificate obtained from a trusted authority, do the following:
- Click the Generate certificate request button. The Generate New Certificate dialog opens.
- Fill in the required details and click Save .
- Once the certificate is ready, a window will pop up with the certificate request information.
- Click Copy to copy the request, so you can later send it to the certificate authority.
- Once you receive the SSL certificate from the certificate authority, click the Import public key button on the SSL/TLS tab page.
- Browse for the certificate file containing the public key and click Open .
- Click OK to save the settings.
Securing RDP-UDP Connections
A Parallels Client normally communicates with a RAS Secure Client Gateway over a TCP connection. Recent Windows clients may also utilize a UDP connection to improve WAN performance. To provide the SSL protection for UDP connections, DTLS must be used.
To use DTLS on a RAS Secure Client Gateway:
- On the SSL/TLS tab page, make sure that the Enable SSL on Port option is selected (default).
- On the Network tab page , make sure that the Enable RDP UDP Data Tunneling option is selected (default).
The Parallels Clients must be configured to use the Gateway SSL Mode . This option can be set in the Connections Settings > Connection Mode drop-down list on the client side.
Once the above options are correctly set, both TCP and UDP connections will be tunneled over SSL.
|
|
 Feedback
Feedback
|